Some of us here at Athena Alpha have worked in IT and Telecommunications companies for literally decades. We are well versed in cyber security, Home Network Security and have even disclosed significant data breaches to major organizations before.
From that real world experience we know that protecting your home network and connected devices is an exceptionally hard problem to manage. But it’s also something that must be done and is even more important for those securing Bitcoin. So in this piece we’re going to take you through a whole host of ways you can protect not just your bitcoin, but all your devices, data and family too.
Contents
What Is Home Network Security And Why Should I Care?
Home Network Security refers to the protection of your entire home network from outside threats such as hackers or malware. This protection covers a huge range of equipment like your main wireless router, computers, mobile devices, IoT devices, servers, various types of media such as HDD’s, SSD’s, CD’s, DVD’s, SD Cards, USB Flash Drives and especially Bitcoin related things like Hardware Wallets.
>> Learn More: A Beginners Guide To Bitcoin Security
Securing your home network is absolutely critical when it comes to protecting your personal information and wealth. Attackers who get in can steal or corrupt everything from your bitcoins to your fiat to your personal information like medical records, family photos, tax records or even just your game collection. One of the worst results is identity theft, where they’ll pretend to be you and sign you up for thousands in debt!
As everyone’s home is connected to the public internet 24/7 now it makes you far more vulnerable to these outside threats. Although it’s not fair to expect the average person to be a full blown cyber security specialist, you don’t really have a choice anymore unfortunately. You either learn to properly defend yourself in cyberspace, or eventually you’ll suffer the consequences. So let’s get teaching!
Accounts, Passwords & Multi Factor Authentication (MFA)
Your account management, password strength and uniqueness is the most important of all the below security measures. You can have the best equipment that’s hardened to NIST security standards and it’ll all be irrelevant if your password is “12345678” or some other easily guessable or common combination like your birthday or something.
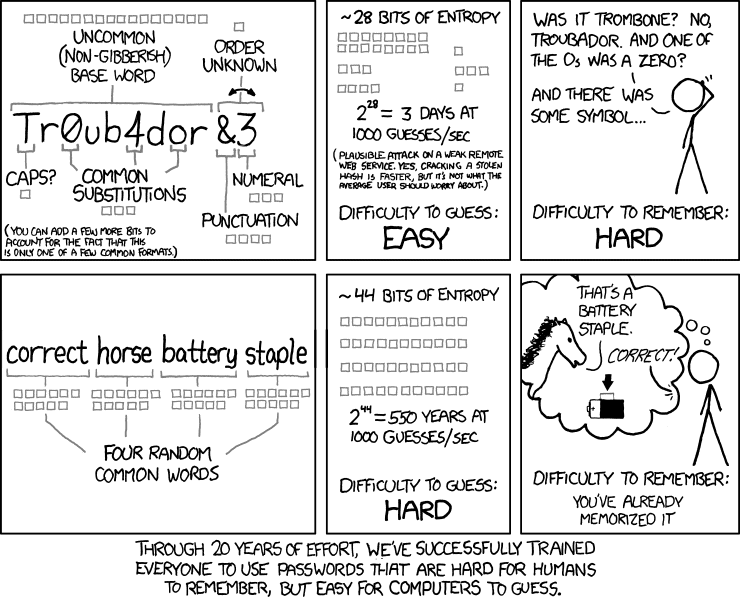
Password Manager & Passphrases
That’s why you should absolutely be using a password manager to generate and store long, unique and random passwords for all your accounts. A great option is Bitwarden. It’s open source and offers free personal accounts plus you can even host your own Bitwarden compatible server (called Vaultwarden) and ensure all passwords never leave your control if you want.
Ideally your master password should be a long passphrase (20+ characters) made up of 5 or more words. The words should be random and not part of a sentence or common movie or song. Passphrases are an excellent way to have extremely long, but generally easy to remember password.
Multi Factor Authentication (MFA / 2FA)
Every major account (especially your password manager) that protects something of value should have MFA enabled on it. We’re talking core recovery email accounts like Gmail or Outlook along with anything that houses finances or private health information. If the account supports it, use it!
SMS based MFA is better than nothing, but App based is far better if you have the option as it’s not susceptible to SIM Swap attacks which are all too common in America. Some good options include Aegis, Authy or even Google Authenticator. Just make sure you turn off any “sync” functions!
Don’t Change Passwords
A common “tip” many even in the security or IT areas give is to be constantly changing your passwords every X months. This is in fact old and bad security advice! If someone is forced to change their password constantly, it just ends up in them creating very weak passwords with predictable patterns like <password1>, then <password2> etc. Even the US government cyber security experts note this!
Verifiers SHOULD NOT require memorized secrets to be changed arbitrarily (e.g., periodically).
NIST 800-63B – Digital Identity Guidelines, Section 5.1.1.2
While you should absolutely change passwords if you suspect there’s been hacking attempts or someone has gained access, changing it for no reason is a bad idea.
Instead, focus on ensuring you have MFA turned on and that your passwords are long and unique for each account which is made easiest by using a password manager as described. Never use the same password for any accounts!
Home Network Security

Get A Good Router / Gateway
You’ve probably got one of those internet service provider supplied wireless routers. A cheap, plastic piece of garbage that barely has enough processing power to blink the LED’s on it, let alone monitor and protect you from the horror that is the public internet.
Your main wireless router is likely what you connect your internet modem to and it’s not uncommon for them to include a WiFi access point, switch and even firewall too. While it’s outside the scope of this article to discuss appropriate gateway devices, just know that you get what you pay for. So pay for something good as it’s one of the key pieces of equipment that protects you.
Some excellent router brand options include companies like UniFi, TP-Link, Asus or Synology. These will not only give you more powerful router settings to help manage your network, such as a firewall or Intrusion Detection and Prevention (IDS/IPS), but will last longer and provide a better user experience too. While setting it up, make sure you change the router’s admin default password and use a strong, long, random password from your password manager.
Segregate Your Networks With VLANs
With your new, more powerful router, create multiple separate Virtual Local Area Networks (VLANs). Create one for your core, secure devices like your mobile phone, laptop or desktop. Create another for all the atrociously insecure IoT devices, like smart TVs, you likely have. Add all the cameras to another one. Got a work laptop or have guests that come over and use your network? Those all go on your Guest network.
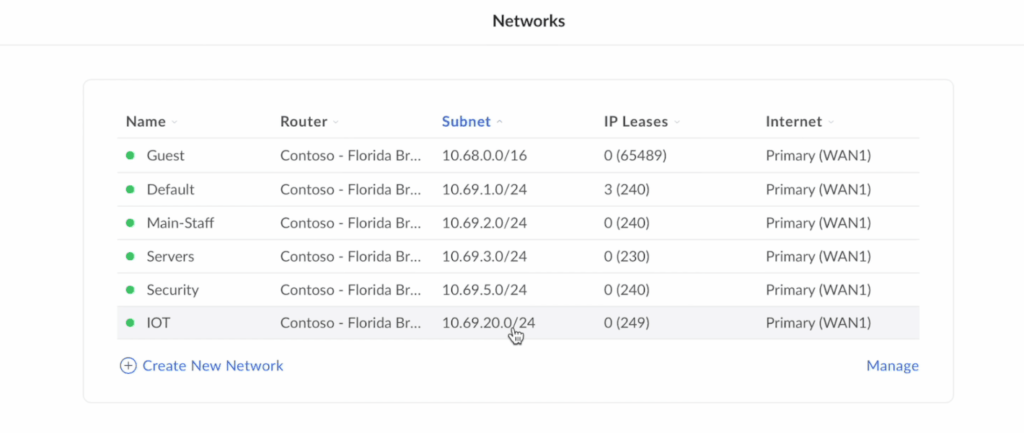
The above image is from an excellent full network setup and configuration guide you can find here. Although it’s obviously demonstrated on UniFi equipment, it can be done on many other top tier routers and is a great step-by-step guide on how to really segregate and lock down your network.
Having different connected devices locked to a separate network means they cannot connect or communication to other devices. This means if someone compromises your smart home devices, they can’t then go and infect your laptop or see all your camera feeds.
While setting up multiple networks can get a bit complicated for many people, it’s something most people can figure out with a few YouTube videos and a router that’s got a good user interface such as the ones suggested above. Do note that you will need a reasonably top tier level router for this as it requires a bit of processing muscle.
Enable Additional Features & Automatic Updates
Go through and learn about all the features you can enable to harden the router and your network. Many good quality routers include VPNs, automatic and regular security updates that keep your router protected from new threats, parental controls or the previously mentioned Intrusion Detection and Prevention systems which will scan each packet that goes in and out for suspicious activity and actively block unauthorized devices for you at a network level. While you’re there, make sure to turn your router’s firewall on.
You can even start running things like Pi-hole or AdGuard on your own server or Raspberry Pi. These servers block advertising and tracking across all devices connected to the network which can often be the source of malware or viruses.
There’s also a number of things you can turn off as well to harden security. For example, if you’re not using features like universal plug and play (UPnP) turn it off. Most routers make it fairly simple to just disable these features such as remote access or analytics by browsing to the menu and clicking disable.
Wi-Fi Network Security

Proper Wi-Fi network security is another major component that protects your home. Make sure your home Wi-Fi network is using at least WPA2 security, preferably WPA3 if all your connected devices support it (spoiler: they won’t, especially IoT devices).
Set the passwords for the Wi-Fi networks to be strong, random, unique and long. This shouldn’t be your mobile number, birthday, dogs name or something that’s only 10 characters long. It shouldn’t even be a word!
Aim for a randomly generated 20+ characters or more combined with all the trimmings of upper case, lower case, punctuation etc. An easy way to add a bit of randomness is to hash a random bunch of characters or dice rolls a bunch of times over and use the result. Is it a pain to type a long, random password into everything? Yes. Is it something you only really have to do once? Yes. So don’t be a slacker.
Also consider the connected devices that are permitted on your local network carefully. Many spy on and send diagnostic metrics back to their manufacturer (looking at you Windows!), so it’s a good idea to separate these unwanted devices you can’t control into separate VLAN’s as noted earlier and keep an eye out for any new device that pops up unannounced.
Guest Network
It’s also recommended to have a Guest Wi-Fi network too. This can be used for any relatives or friends that visit as well as any work devices that you use working from home. This again segregates these “untrusted” devices off your main, secure network and onto an isolated network that cannot infect anything.
Home Computer Security
Now that your accounts and network security is much improved, let’s look at your actual computers. These are the things in your home networks that you can actually control and configure like laptops, phones, desktops or servers.
Keep Your Computers Clean

It’s simple, yet incredibly powerful advice. Make sure you install the least amount of apps possible on phones or laptops. With every app you get another hole in your security, plus it slows your computer down too.
There’s been a big push over the years to always download and install “the app” for whatever it is you’re trying to do. Want to browse Reddit? Get the app! Twitter? App! eBay? App! Instead make it a point to use the website instead and forgo the app install. You’ll find more often than not it’s an identical user experience and it’s one less thing that’s got who knows what access to your computer.
Going further, make sure to remove any unneeded accounts, applications, services or functions on the device to again pair things back as much as possible. This should also include any user data which should be instead kept in a single, central location such as a NAS.
Ideally your devices shouldn’t have much, if any user data on them and you want to be running on as close to a stock setup as possible at all times. This has a number of advantages such as:
- If your device is compromised there’s no sensitive information or configuration info to steal
- If your device is compromised you can simply reformat it and be back up and running quickly
- Setting up or moving to new devices is simple and quick
- As there are fewer programs running, the attack surface area is significantly less
- You don’t need to always be changing settings or configurations
- If your device breaks or is damaged there’s no loss of user data
Keep Up To Date
Another easy one, setup and turn on automatic updates on as many routers, computers, phones or systems as you can to make sure you’re always up to date. On this same topic, ensure your devices are new enough to still get current security software updates. Have the latest OS installed on it, preferably Linux or Mac, and ensure the entire drive is encrypted from boot.
Going further ensure Secure Boot and Trusted Boot functionality is enabled and if you want to, have some good quality antivirus software installed too. By default Windows has decent antivirus software already built in these days, but it doesn’t usually hurt to have more if you want.
Mobile Devices
Mobiles are a bit unique as protection is required not just inside your home but outside too given they’re taken with us everywhere.
Setup A Strong, Random Password
To start with, make sure your mobile has a strong, unique password (not a pin!) lock on it. Aim for 16+ characters and make it something random, preferably some random numbers generated by your password manager.
Consider What Data You Keep On It
Next is to give some serious consideration as to whether or not it needs any Bitcoin wallet or crypto related apps or information on it at all. While mobiles are kept with you, they can also easily be lost or stolen, so making sure the thief doesn’t then have access to or knowledge of your Bitcoin funds is important
On top of this, make sure you’re able to remotely wipe all data off it just in case it does ever get lost or stolen. Losing a phone is bad enough when they’re often $1,000+, knowing that someone else might now have access to your bitcoin funds or have all your naked selfies is even worse.
Your Mobile Always Stays Within Arms Reach
Another extremely good recommendation is to always ensure your mobile is within arms reach. Leaving the room for a second? Take your phone. Stepping away from your desk at work to chat with Bob? Take your phone. Going to the toilet? Take your phone.
While it’s obviously not a huge risk to leave your phone unattended at home, creating the habit ensures you never leave it unattended in public. Your phone has some of the most sensitive, personal data on it and is the most susceptible to loss or theft. Never allow untrusted people to hold, use or connect to your phone and always keep it within arms reach.
Avoid Public WiFi
A free or public Wi-Fi network can be great… but also introduces many potentially bad actors that can intercept and spy on traffic. At a bare minimum, try to avoid using them with the computer that has your Bitcoin wallet on it. If you do have to use one, try and avoid sending sensitive information over it and use a VPN.
While in these type of public places never connect your mobile to charging stations or wall outlets. Charge via a laptop you own or using a battery bank instead as that random public USB plug can send more than just power to your phone!
Finally when in public just be more generally aware of what you’re doing on your phone. It’s easy for people or surveillance cameras to shoulder surf and record your passwords as you enter them. Even once logged in you don’t want strangers to see things like your exorbitantly large bitcoin balances, so either hide your screen well or better, wait until you’re somewhere private.
FAQ
How Can You Protect Your Home Computer?
Keep your computer clean with as few apps installed as possible. Keep your operating system and the installed apps up to date with any software or firmware updates and ensure they’re protected with strong, unique and long passwords. Finally make sure it’s connected to a secure home network, using WPA2 or WPA3 if connected via WiFi and be sure to disable remote access if it’s setup.
How Should You Secure Your Home Wireless Network?
Ensure your Wi-Fi network is setup using a long, unique password that’s made up of random numbers and letters. Your Wi-Fi password should be randomly generated and 20+ characters long. The Wi-Fi network should also use WPA2 or WPA3 and have separate networks for things like the home network, IoT devices, cameras as well as a guest network.
How Can You Prevent Viruses And Malicious Code?
The best way to avoid viruses or other malicious cyber actors from installing malware on your compute is to install as few apps and services as possible, as well as being sure to never click on links or files such as Word or PDF’s that you receive via email. Windows now has antivirus software already built into it, but having a secondary software package can help too.