In our first piece in this three part series we covered a number of different design considerations you should be aware of when dealing with Expert Cryptocurrency Security. Now that we’ve got a good handle on what our top priorities should be, we’re going to dive deeper into what some of the leading best practices are in the crypto industry when creating Bitcoin Multisig Vaults.
These are the procedures and standards that massive custodians like Coinbase or Unchained Capital use to custody, quite literally, billions in bitcoin. We’ve read through them all, cover to cover, and condensed the information down into simple and actionable points so you don’t have to. Let’s get started!
This is the second part of our Expert Bitcoin Multisig Vault series. You should read the first part (Expert Cryptocurrency Security) before continuing and then read the third (How To Setup A Bitcoin Multisig Wallet) part after this.
Contents
Bitcoin Multisig Industry Standards
Requirements for the design, generation, setting up, storage and operation of crypto custody solutions for the huge companies that custody billions of dollars in bitcoin are based off these documents or ones very similar in nature:
- Cryptocurrency Security Standard (CCSS)
- Unchained Capital’s Operational Security Guide
- Glacier Protocol
There are obviously far more standards out there, but after reviewing these and many others, there’s a general trend in the most important parts of self custody, security and ongoing maintenance. These are three of the best and most open standards out there and we’ve broken them down into three main categories: Seed Generation, Wallet Creation and Seed Storage.
Each section below has a list of recommended requirements that you should strive to meet when designing your own custody solution. In the third and final part of this series, we’ll propose a Bitcoin multisig vault solution that meets these requirements and that you can personally setup all for a one time, up front cost of about $500 USD.
Seed Generation
Paramount to a bitcoin wallets security is precisely how it generates your Private Keys as this is what everything is derived from. To securely create cryptographic keys and seeds requires confidentiality and unpredictable numbers.
Confidentiality is required to ensure that the newly created keys or seeds are not read/copied by an unintended party. Nondeterministic and unpredictable numbers are required to ensure the newly created key cannot be guessed or determined by an unintended party.
In order to ensure both of these requirements are met it’s recommended:
- Private Key Generation Software: The software that’s used to generate your Private Keys, whether it’s on a PC, phone or Hardware Wallet, should be validated as secure prior to use. The software shouldn’t restrict which characters or numbers can be used during generation and it shouldn’t store or transmit any data to a third party
- Private Key Ownership: You should be the only one generating the Private Keys and they should be generated in your presence. They should not be generated for you prior and no one else should be present at the time of creation
- DRBG Compliance: The Private Keys should be generated using cryptographically secure hardware such as a Deterministic Random Bit Generator (DRBG) that conforms to NIST SP 800-90A, a Non-deterministic Random Bit Generator (NRBG) or a “True Random Number Generator” (TRNG) that passes industry-standard statistical tests for randomness such as DIEHARD, Crypt-X, or NIST STS. These number generators should also be seeded with at least two separate cryptographically secure sources of entropy that have been combined in a cryptographically secure manner. Private Key generation should also include unique, just in time randomness from a real world random source such as resistor values, radio waves, a picture taken on boot or user inputted randomness from things like dice rolls
- Multi Key Generation Software For Multisig: If multiple Private Keys are being generated for a multisig wallet, ensure that there are enough different key generation software protocols used so that if one is compromised, it won’t have authority to spend
That might all sound like quite a lot of complicated requirements, especially the DRBG compliance part, but in practice it can be quite simple. For example, if you are wanting to generate the private keys and seeds for a 2-of-3 multisig wallet you could:
- Use 3 different branded, well vetted Hardware Wallets to generate the 3 private keys
- Ensure you’re the only one in the room and generated each of them yourself
This would comply with all requirements and give you an extremely solid starting point.
Wallet Creation
This aspect covers the creation of wallets or addresses that can receive your bitcoin. Wallets are created using the Private Keys you’ve just created and can be for a single key, a single key with a Passphrase or multiple keys for Multisig Wallets.
As this is for serious investment amounts and the Expert level, we’ll be focusing on these multisig wallets. While most standards don’t specify what the M or N values should be in a M-of-N multisig wallet, the following requirements should be met:
- Signing Requires Multiple Keys: Any bitcoin addressed generated by the wallet software must require a minimum of 2 signatures in order to spend the funds. There are many reasons why multisig is better than single signature architecture or many of the more complicated single signature setups that use Passphrases, XOR, SSS or other custom designs. For custody of significant funds, it’s highly recommended a multisig wallet is used
- At Least 1 Redundant Key For Recovery: There should be at least 1 redundant keys assigned to the wallet for recovery purposes. One common method of achieving this goal is to create a wallet that requires any 2 of 3 possible signatures in order to spend funds (i.e., there is 1 redundant key). Be aware that for most regular people, a 2-of-3 multisig wallet is better than 3-of-5. While 3-of-5 does allow for more key redundancy in theory (2 instead of 1), in practice it requires more keys, more Hardware Wallets and more locations leading to a more complex custody solution overall and usually less security at each of the many locations. Industry best practice is to use 2-of-3 and not anything higher as it has the best balance between security and complexity. It’s also not recommended to use setup where N = M, for example a 2-of-2 wallet as these do not have any redundant keys
- Documented Wallet Creation Policy: Creation of the wallet should be documented in clear and simple instructions that spouses, children or others can easily follow. A documented custody policy also provides transparency and consistency that helps limit errors
Again the formal outlining of these requirements might sound like a lot, but at the end of the day you can easily tick off all of them by having appropriate documentation of how to create your wallet and use a 2-of-3 multisig wallet.
Seed Storage

A securely generated seed means nothing if it’s not managed and stored properly. Arguably the most complex part of the requirements, storage of the various Private Key elements is a critical and difficult part of designing a custody solution.
By separating the wallet’s keys across multiple locations, any risks associated with localized disruptions such as fire, flood, earthquake, break-ins or accidental key losses don’t affect your ability to spend the funds.
Ideally, each Private Key element (the Hardware Wallet or Recovery Seed) should be stored in a physically different, secure location. For a N-of-M multisig wallet, this means you need 2 x M secure locations. For example, this is what a 2-of-3 wallet would look like ideally:
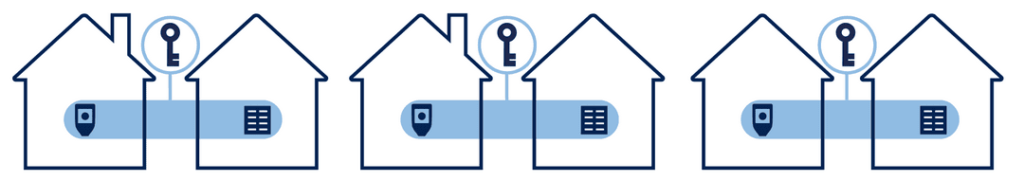
As there’s 3 Private Keys (M), this means the most secure way to store them is in 2 x 3 = 6 different locations. Many people, understandably, have trouble coming up with this many locations! Maybe you’re rich af and have six separate properties scattered around the globe, but most don’t!
If you want a 3-of-5 multisig wallet, now you’ll need 5 x 2 = 10 different secure locations which is even worse! This is one of the main reasons why it’s recommended to not use 3-of-5 multisig wallets. The additional location requirements in practice often results in a high number of lesser secured locations rather than a low number of higher secured locations.
To help ensure secure storage of a Private Key element, whilst not creating unrealistic expectations like above, some recommendations locations include:
- At home in a fireproof safe that’s bolted to the floor
- A secondary location on your property, far enough away so that multiple Private Key elements wouldn’t be destroyed or compromised by a burglary or natural disaster
- At a second home you own in a fireproof safe that’s bolted to the floor
- In a Private Safety Deposit Box (PSDB). This should not be a bank safety deposit box and should only be for multisig wallets. Also ensure you avoid holding two Recovery Seeds or Hardware Wallets with the same provider
- At a trusted family members home, in a fireproof safe, bolted to the floor and only for multisig wallets (also ensure you read the Expert Cryptocurrency Security guidelines on what to consider when involving family or friends)
- At a work place, so long as it’s secured in a lock box, locked locker or other physical access controlled area
Bad storage locations for Private Key elements, sensitive data such as passwords, PINs, wallet software information such as receive addresses or their backups that should be avoided include:
- Out in the open such as on a desk, in your bag or in a filing cabinet
- In a desk drawer, cupboard or shelf either at home or at your workplace
Whatever storage locations you choose, you should be ensuring they meet as many of the below requirements as possible. This is a big list with them all being highly important. Don’t let the idea of a perfect plan be the enemy of a good plan though. It’s likely you won’t be able to meet all of these requirements, try your best and hit as many as you can:
- Private Keys Must Be Stored Encrypted: All Private Keys must be stored using strong encryption when not in use. Industry best practice for this is to store the Private Key on a Hardware Wallet that protects it using one or more Secure Elements and PIN
- Backup Private Keys Must Exist: A backup of each Private Key must exist. While you can have extra backups such as on a microSD card, there should always be a Recovery Seed phrase card (paper or steel) backup at a minimum. Hardware Wallets, just like all other hardware devices, fail all the time for many, many reasons such as due to bitrot, the user forgetting the devices PIN and/or having the device wipe the seed, losing seed phrases, firmware updates that fail and more. A backup must exist for at least as many keys as are required to spend funds. For example, in a 2-of-3 signing setup, backups must exist for at least 2 of these keys. While there must be at least 1 backup, industry best practices for data storage is a 3-2-1 Strategy with 1 redundant copy. A 2-of-3 multisig wallet already enables the equivalent of this 1 redundancy, but you should still have:
- 3 Copies Of The Data: Maintain three copies of data (the original and two copies)
- 2 Different Media: Use two different media types for storage
- 1 Copy Offsite: Keep one copy offsite to prevent data loss due to a site-specific failure
- Primary & Backup Keys Are Not Co-Located: Each primary Private Key and its back up must not be co-located in any combination of Hardware Wallets or backup recovery seed while in storage. For example, 3 Hardware Wallets and 3 Recovery Seed cards should be stored using 6 unique locations. Even if your Hardware Wallet and Recovery Seed are protecting the same seed, keeping them separated can afford you maximum opportunities to recover your funds before an attacker gets them. Ideally one Recovery Seed would also be held in a far away, different geographic location (different city or state), whether it be held by a trusted family/friend or in a safe deposit box
- Backup Keys Are Encrypted: Backups of Private Keys and/or Recovery Seeds must be stored with the use of strong encryption when not in use that is at least equal to the security of the primary. The exception for this is of course, a written Recovery Seed phrase card where it’s just 12 or 24 words written down and thus, not encrypted
- Private Keys Have Environmental Protection: Private Keys must be protected against environmental risks such as fires, floods, earthquakes and other acts of God. Common methods to achieve this include water-tight bags for flood protection and a fireproof safe for fire protection. The backup key/seed must be stored in a location that is geographically separate from the usage location of the primary key/seed. For example, if the primary key is kept at home, the backup key could be in escrow with a trusted 3rd party. Backups should also be resistant to electromagnetic pulses that could induce currents in electronics and damage the data stored within. A common methodology to secure against this risk is to store a seed or key on laminated paper or metal plate.
- Private Keys Have Physical Protection: Access to the Hardware Wallet devices or Recovery Seed phrase cards must be physically protected, for example a fireproof safe, bolted to the floor or a Private Safety Deposit Box (PSDB) at a secure location with guards, 24/7 monitoring and locks. Multiple safe deposit boxes within the same company may be used, however this is not ideal
- Private Keys Are Access Controlled: The Private Key elements must be protected by access controls that prevent unauthorized parties from accessing it. Examples of this include safes, safe deposit boxes, or locked drawers where only the operator holds the key/combination for the lock
- Private Keys Have Tamper Evident Seal: The Private Key elements must employ some form of tamper evident mechanism that allows you to know if it’s been accessed. A secure method of achieving this involves a serial-numbered tamper-evident bag
- No Keys Stored On Mobile Devices: Although it’s common and often convenient to store Private Keys on mobile devices, they are heavily exposed to remote threats and are easily lost, meaning more headaches and greater risk. Storing a key to a material portion of your wealth on an online device that you regularly carry on your person is an unacceptable compromise and should be avoided at all costs. Instead, only use mobile wallets for small amounts of funds that are separate to your main multisig vault
- Trusted Signatories Don’t Control M Keys: Ensure that the distribution of your Private Keys doesn’t allow collusion of the other trusted parties such as family or friends to reach the spending threshold M. For example, in a 2-of-3 wallet, don’t have 2 trusted parties as they can collude together and steal your funds without you being able to stop it. This also ensures that if all signatories fail to properly secure their Private Key elements or simply lose it, your funds are also still protected
As said earlier, this is a big list. Unless you’re rocking 10 figures plus, it’s unlikely you’ll be able to satisfy all of them, so don’t feel bad if you can’t! An example of a seed storage setup for a 2-of-3 multisig wallet that’s highly secure might be:
- Each primary Private Key is encrypted and stored in a Hardware Wallet
- Each Hardware Wallet has a encrypted microSD card backup
- Each Private Key has a Recovery Seed in the form of a metal seed plate
- This provides 3 copies, on 2 different media with 1 of them kept off-site for each Key
- Private Key elements are split up and stored in a tamper evident bag
- Storage locations are chosen to be the persons home, their vacation property, a family members home and a rented safety deposit box
- All bags are stored in a safe or lock box in a cool, dark, dry, hidden location
What your storage locations look like will obviously be very different, but always remember to take into account the various considerations we covered in the first part of this series. What locations are most risky for theft, natural disaster or accidental loss? Think of these considerations, plan as best you can and don’t be too concerned if it’s not 100% perfect.
Testing Your Bitcoin Multisig Solution
Once you’ve come up with a few potential designs for your custody solution, it’s a good idea to run them through as many hypothetical scenarios as possible to evaluate their robustness. For example, what happens if your entire house burns down? What happens if two of your storage locations are compromised simultaneously?
Obviously the number of possible combinations and simulations you can run is near endless, and your custody solution designs likely will never hold up against all of them perfectly. But by running the same tests against multiple different proposed setups, you can easily figure out which one is the best.
To help with this, we’ve outlined a number of tests you can apply broken down into two categories:
Security & Physical Duress Resistance
Possibly the most extreme tests, this section evaluates your design against “attackers”. This could be a lowly common house burglar that’s just picked your house at random or a much more advanced adversary that is specifically targeting you as they know you have bitcoin, own a Hardware Wallet or suspect you have considerable funds. These attackers could also conceivably be police or government agents too.
Decryption keys refers to things like Hardware Wallet PINs, software wallet passwords or the passwords that decrypt wallet backup files. So how does your custody setup perform when:
- Attackers raid 1 location, get all Private Keys not in safes, but don’t have decryption keys
- Attackers raid 2 locations, get all Private Keys not in safes, but don’t have decryption keys
- Attackers raid 1 location, get all Private Keys even in safes, but don’t have decryption keys
- Attackers raid 2 locations, get all Private Keys even in safes, but don’t have decryption keys
- Attackers raid 1 location, get all Private Keys even in safes and also gets decryption keys
- Attackers raid 2 locations, get all Private Keys even in safes and also gets decryption keys
- Attackers go visit other family members locations
Raiding of 2 locations might occur due to them invading your home and then taking you to another one of your seed storage locations at gun point. That other location might also be a family members house. These are tough and extreme scenarios to consider.
Ultimately to best protect against these types of threats, your custody solution must require significant time and/or distance as well as your identity to be confirmed in order to gain the ability to spend funds (ie. have M number of keys).
For example, maybe the attackers need to drive 1,000 miles to get the 2 keys needed for your 2-of-3 multisig wallet. Maybe your wallets have time lockouts on them or maybe you need to pass through a safety deposit box check point that has guards with guns, locks, safes, cameras and more in order to acquire the needed number of keys.
Whatever the case, the above tests will help to expose your designs weaknesses and enable you to build a highly secure setup.
Acts Of God & Accidental Loss Resistance
Next up we have a number of slightly less lethal tests, but ones that are still very important and also a lot more likely to happen. As noted in part one, you are your own worst enemy. People forget passwords or PINs and often mistakenly throw Hardware Wallets, storage media, computers or pieces of paper (Recovery Seeds) out all the time and it often results in them losing their Bitcoin.
These tests cover acts of God such as fires, floods, earthquakes, storms and more. Maybe a huge tree lands on your house, maybe you come home to find your house is now a pile of ash. Once again, go through each of these and assess how your design fairs:
- Act of God destroys 1 location or you’re never allowed to access it ever again
- Act of God destroys 2 locations or you’re never allowed to access them ever again
- Act of God destroys 3 locations or you’re never allowed to access them ever again
- You forget the PIN to all 3 Hardware Wallets and any encrypted backups
- You loses all Wallet Output Descriptor files and backups and have to rebuild the multisig wallet only using the Recovery Seeds
- Act of God destroys your Home location, all its contents and you are also killed
- You and your spouse are both killed in a car accident
- War breaks out in your city, the entire CBD area is bombed or closed off for months and you’re forced to flee to another city/county
Building The Dream
As you can no doubt tell, building a custody solution that securely stores your precious bitcoin is actually a very involved task. Even when using the best practices from industry giants there’s still a lot to consider, plan for, keep in mind and learn.
From day one, we’ve always sought to make bitcoin simple and easy for our readers. While reading about all the above requirements and standards is interesting and excellent to teach you how the cake is baked and why it’s baked in the specific way it is, it’s not a simple turn key solution.
So in our final part three, we’re going to do exactly that. We’ll take you through, step-by-step, and show you how to setup a 2-of-3 multisig wallet vault that gives institutional level grade security all for a one time, up front cost of about $500 USD.
>> Third Part: How To Setup A Bitcoin Multisig Wallet