The first step when getting into Bitcoin is to get a wallet, but there’s so many types! Which one do you choose? Which one is the safest? Which is the most private? And how are cryptocurrency hot wallets different from cold wallets? Let’s have a look.
>> Ready for a wallet? Here are our top picks!
Contents
What Is A Bitcoin Wallet?
A Bitcoin wallet is simply software that:
- Generates and manages your Private Keys, which gives you access to spend your bitcoins
- Generates and manages your Bitcoin Addresses, so you can receive bitcoins
- Creates and broadcasts transactions to the Bitcoin network so you can spend your bitcoins
They come in many shapes and sizes such as software wallets (exchange, web, desktop or mobile), hardware wallets (cold, air gaped, USB) and multisig wallets. Today though we’ll specifically be looking at a hot wallet vs cold wallet comparison and why you might chose one over the other.
What Is A Hot Wallet?
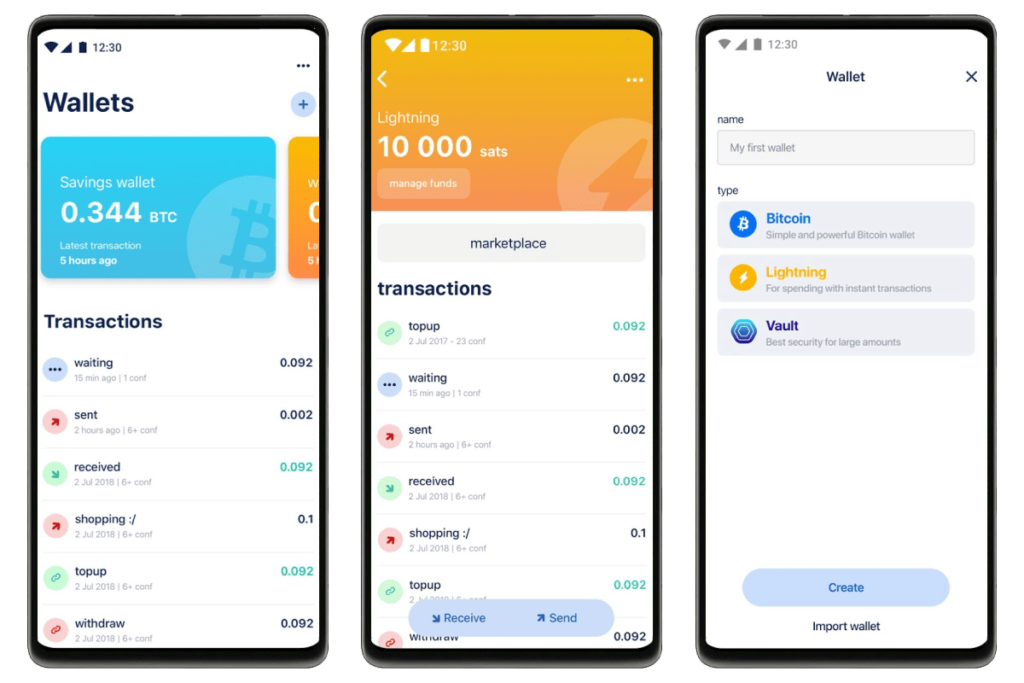
A hot wallet is a software program that runs on any computer, phone or exchange and that stores your private keys in the software program itself, meaning it and your keys are always connected to the internet.
They can be custodial or non-custodial and most Bitcoin wallet software out there is a hot wallet. As the private keys can be accessed via the internet, they are highly vulnerable to malware and hackers. It is not recommended to keep large amounts of funds in hot wallets.
What Is A Cold Wallet?

A cold wallet is a software program that runs on any computer, phone or exchange and that stores your private keys in a separate, offline hardware wallet device, meaning it and your keys are never connected to the internet.
They can be custodial or non-custodial and as they store private keys physically separate from the software on the hardware wallet, they are highly resistant to malware and hackers. The term “cold storage” or “deep cold storage” relates specifically to the fact that your private and public keys that make up your cryptocurrency wallet aren’t connected to the internet.
A wallet is considered deep cold storage when the cold wallet device (and thus crypto keys) are kept in a highly secure, locked away place that takes a lot of time and effort to access such as in an offsite safe or in a different city entirely. This is typically used for funds in long term storage.
New to Athena Alpha? Start today!
How Are Cryptocurrency Hot Wallets Different From Cold Wallets?
One of the biggest risks to keeping your bitcoins safe has always been hacking, scams or social engineering which software of all types is highly susceptible to. To help users combat this cold storage wallets were created.
Going by many names such as Hardware Wallets, Signing Devices, Cold Storage Devices, Cryptocurrency Cold Storage or Cryptocurrency Cold Wallet they all use dedicated pieces of physical hardware that generate, store and manage your private keys as well as sign transactions for you.
By separating your private key onto a physical hardware device, away from your disgustingly malware infested computer that’s running the software component, it drastically increases the security of your bitcoin storage setup.
When your private keys are stored on a cold wallet, a hacker can get full control of your computer or phone and all they can do is view your wallet funds. In order to steal (or spend) your bitcoins they would need your Hardware Crypto Wallet to be plugged in and unlocked.
Then they’d also need to push physical buttons on it too somehow. This extra physical layer makes hacking attacks much harder to execute, but also decreases how user friendly the wallet is.
Advantages & Disadvantages Of Hot Wallets
Pros:
- Free, quick and easy to setup and use
- No need for a physical device to spend funds
- Great for experimentation, beginners, testing and those performing regular transactions
Cons:
- Your public and private keys are connected to the internet putting your digital assets at risk
- Absolutely not safe from hacking, phishing, malware, viruses or other cyber security threats
Advantages & Disadvantages Of Cold Wallets
Pros:
- Your public and private keys are not connected to the internet keeping your digital assets safe
- Can be completely air gapped and never connected to any computer at all if you want
- Great for storing “Savings Level” of funds
Cons:
- Costs money and requires the purchase of a hardware wallet to use
- Requires the physical use of the device every time you need to do crypto transactions
- Can be more complex for beginners and requires more research to learn about and use
Things To Know When Buying Cold Wallets
You should only ever purchase a cold wallet device directly from the manufacturer, never second hand! It should ideally come in a tamper resistant bag, be open source and well respected and vetted by the community. You should also try as hard as possible to ensure the name, address and funds used for the purchase are not linked in any way to your real identity.
This is because if the manufacturing company gets hacked, and the hackers get a list of all their customer names and addresses, those hackers will then know your identity, address and that you own enough bitcoin to make owning a hardware crypto wallet a priority. Not good for your safety!
The leaking of information also often results in huge influxes of crypto specific spam literally forever. These try and get you to click malicious links, claim your account has been locked, ask for your seed phrase or use other social engineering techniques to steal your funds.
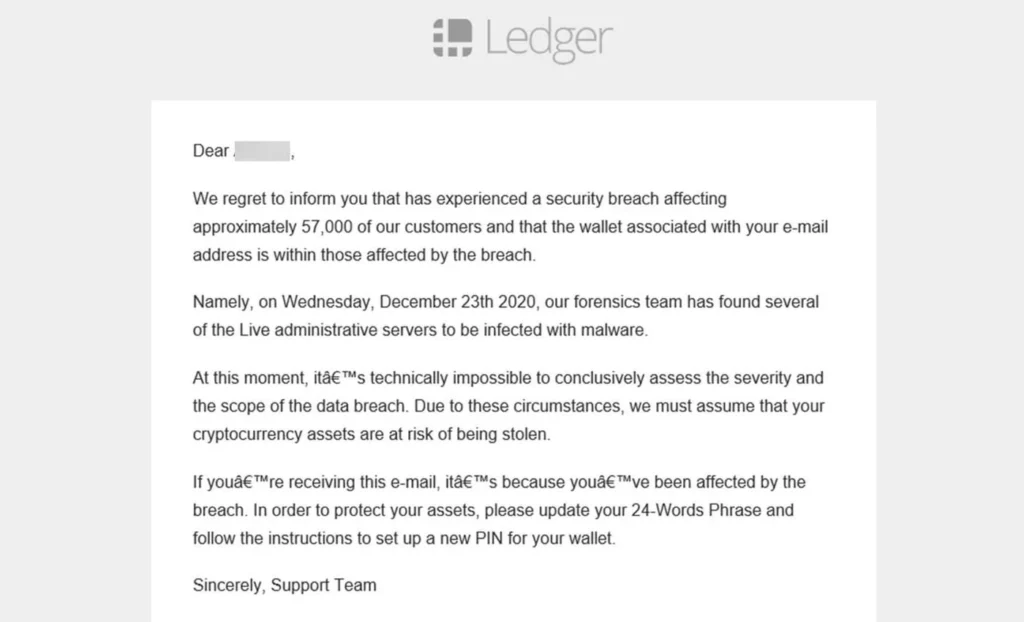
A simple and free way to do this is to create a brand new Proton Mail account that you only access via Tor Browser. Then use this one time email (and a fake name) to purchase your device online with Bitcoin (preferably over the Lightning Network).
While finding a delivery address that’s not linked to your identity can be a bit harder, there are many options like PO Boxes, delivering to a work place or some other temporary location.
Popular Cold Wallet Options
| Wallet | Learn More | Athena Alpha Rating | |
|---|---|---|---|
 | Jade Plus By Blockstream Bitcoin Only | LEARN MORE | 4.8 / 5 25/25 Privacy & Security |
 | Passport By Foundation Bitcoin Only | LEARN MORE | / 5 25/25 Privacy & Security |
 | COLDCARD Q By Coinkite Bitcoin Only | LEARN MORE | 4.6 / 5 24/25 Privacy & Security |
 | 3 Pro By Keystone Bitcoin + Alt Coins | LEARN MORE | / 5 25/25 Privacy & Security |
 | COLDCARD Mk4 By Coinkite Bitcoin Only | LEARN MORE | / 5 24/25 Privacy & Security |
Wallets Don’t Store Your Bitcoin!
Another important thing you need to know about all Bitcoin Wallets is that they do not store any bitcoins! The name “wallet” is used because the creators of the software are trying to make it easily relatable to everyday people, but in actual fact Bitcoin Wallet software isn’t like a normal “wallet” that might store physical cash or coins. It’s not even like a bank account.
Instead, Bitcoin Wallets only ever store your private keys which is what gives you access to your bitcoins. Every bitcoin is and always has been located on the Bitcoin network. In summary:
- Bitcoin Wallet: Stores your private keys
- Bitcoin Network: Stores your bitcoins
This might seem like a simple distinction, but it’s a critical one that is very important to understand and embed right from the start as otherwise it leads to lots of confusion.
People mistakenly believe that if they uninstall their Bitcoin Wallet software or if their hardware breaks then “all their bitcoins are now gone”. This isn’t true as long as you still have your private keys. Again, there are no bitcoins ever “stored” in your “wallet”, only private keys.
Other Bitcoin Wallet Types
There are a number of different wallet types out there:
- Mobile Wallet: A wallet that runs exclusively on your phone. They can be custodial or non-custodial and even integrate with a hardware wallet device via USB, NFC or Bluetooth for added security. Some examples include Electrum, Nunchuk, Keeper and BlueWallet
- Browser Extension Wallet: A wallet that runs exclusively in a web browser extension program. They can be custodial or non-custodial but are usually non-custodial and don’t use hardware wallet protection. As the private keys are kept in the software, they are highly vulnerable to malware or hackers. It is recommended not to keep a large amount of funds in browser extension wallets.
- Exchange / Web Wallet: A wallet that runs in a website, similar to how a bank runs your bank account. These are usually custodian and don’t use hardware wallet protection. They also introduce third parties (the ones that own the website / exchange) and thus bring even more risks. It is recommended not to keep any amount of funds in exchange or web wallets. Some examples include Coinbase, Binance, Blockchain and BitGo
- Desktop Wallet: A wallet that runs exclusively on your desktop computer. They can be custodial or non-custodial and even integrate with a hardware wallet device via USB, NFC, QR codes or Bluetooth for added security. Some examples include Sparrow, Electrum, Nunchuk, Keeper and Specter.
- Multisig Wallet: A wallet that can only spend the funds when multiple private keys are used together, instead of a single key, avoiding a single point of failure. These private keys can be spread across multiple software and/or hardware wallets, each with their own single private key. They are usually non-custodial, but there are some services which can take custody of one of the multiple private keys for additional security called multicustodial wallets. They are the most advanced wallet type and introduce a few extra complexities in order to increase the security. For example a 2-of-3 multisig wallet might have your private keys spread across three separate hardware wallet devices. Any two are required to move the money, but the loss of any one does not result in loss of money.
Best Practices for Wallet Security
When protecting your digital wallet a number of different forms of security are required. We have a huge array of security orientated articles (see below) that specifically cover all of these different security measures. From malicious smart contracts, protecting your physical device, securing your online environment and especially how to protect your private keys.
The most important thing to always remember though is to never give anyone, under any circumstances, your private key. Anyone who has access can steal all your cryptocurrency wallets funds instantly. Make sure it never interacts or is entered into any computer device, ever!
More Security Articles:
- Home Network Security Best Practices
- 20 Bitcoin Scams: How To Spot And Avoid Them
- How To Protect Your Crypto
- How To Protect Your Bitcoin Private Key
- Expert Cryptocurrency Security
- How To Setup A Bitcoin Multisig Wallet
- Bitcoin Multisig Vaults
- A Beginners Guide To Bitcoin Security
- A Guide To Advanced Bitcoin Security
- A Guide To Expert Bitcoin Security
- Airgap Wallets
FAQ
Are Cold Wallets 100% Safe?
No. While having your private key stored on a hardware device protects you against virtually all malware and hacking vectors, there are still a small number of ways thieves can steal your funds. This usually involves users willingly entering in their private keys to fake websites due to various scams or social engineering tactics. Other less common vectors include supply chain attacks, evil maid attacks or even private key exfiltration via compromised hardware device firmware.
Can Crypto Cold Storage Fail?
Yes. While having your private key stored on a cold wallet protects you against virtually all malware and hacking vectors, the physical devices can still fail due to bugs, hardware failures, drops and falls, exposure to extreme hot or cold temperatures, moisture or even just age or bit rot. For information on ensuring your device has a long and healthy life check out How Long Do Hardware Wallets Last?
Is Coinbase Wallet Hot Or Cold?
Coinbase is an exchange hot wallet. There is no security or privacy as they hold your private keys on your behalf. They have full control over all your funds, can lock you out of them at any time and can see every balance, transaction or anything else you do with your wallet. We strongly recommend to never keep any bitcoin on an exchange.
Is Ledger A Cold Or Hot Wallet?
Ledger is a cold wallet that can be used with their Ledger Live app or via third party wallet software programs on either desktop or mobile. While they have many popular devices, such as the Ledger Nano, we don’t recommend using any Ledger device as they do not meet our strict security and privacy requirements, have failed to protect their users data and have had many questionable practices over the years. See our Crypto Wallets comparison page to find a more secure, more private alternative.
Is MetaMask A Cold Or Hot Wallet?
MetaMask is a browser extension based wallet that supports both hot and cold wallet functionality. You can see their support article on how to use a cold wallet with their platform, but regardless we would still recommend only keeping “Pocket Money” levels of funds in this type of wallet due to its constant exposure to the internet and lack of user privacy.